Until now many variants produced by the virus Ramnit nevertheless this virus has the traits, characteristics and the same action, the parent file name was not changed to keep using the file name WaterMark.exe.
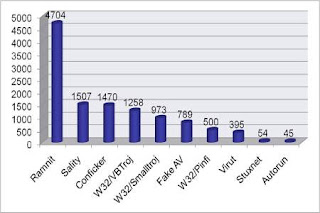
Picture 1. Statistical spread of the virus Ramnet first semester (June 2011),
source: Data Research Vaksincom 2011
Media Distribution
To spread itself, Ramnit will utilize various media such as:
* USB Flash, by creating a file:
o autorun.inf
o Copy of Shortcut to (1). Lnk
o Copy of Shortcut to (4). Lnk
* Create a file in the folder RECYCLER virus with the extension. CPL and EXE files and infects an application (EXE), DLL and HTM / HTML.
* Exploit the vulnerability of Windows MS10-046 http://www.microsoft.com/technet/security/bulletin/ms10-046.mspx KB2286198
* Internet, Ramnit spread over the Internet can occur when a user accesses htm or html file from the webserver that has been injected by Ramnit.
* Network (LAN / WAN) by injecting file EXE / DLL / HTM / HTML on the folder / drive on the share.
Infection targets
At Ramnit infects a computer it searches for and infects files that have the extension EXE, DLL and HTM / HTML in all drives, including removable media. The interesting thing here is Ramnit have the ability to insert the virus code on each file HTM / HTML encountered.
At the time the victim opens the file HTM / HTML that are already infected Ramnit will automatically create a file called "svchost.exe" in the folder [C: \ Documents and Settings \% UsernamePC% \ Local Settings \ Temp]. After successfully creating the file "svchost.exe", ramnit will run the file so it will form a new file with the name "svchostmgr.exe" in the same location, would then create the file "WaterMark.exe" as the master file in the specified location.
File "WaterMark.exe" this for a while will be active in memory and then will mendompleng to the process "svchost.exe" Windows, so the process is performed in memory rather than file "WaterMark.exe" but "Svchost.exe" which will be active with userPC% username% (% userPC%, is the user account that is used during Windows login). (see picture 2 and 3)
Picture 2. Ramnit who boarded the virus in
the process [svchost.exe] Windows and injection files
Picture 3. Windows svchost process that protects Ramnit
With the ability to inject file HTM / HTML (see Picture 4 and 5), will facilitate in an attempt to spread itself, especially if already infected Ramnit Web Server, so that when the user accesses web pages that are already infected the victim's computer will be directly infected by Ramnit.
Picture 4. Injeksi Ramnit di file htm / html
Picture 5. Injection and contains executable files Ramnit own master
If victim execute EXE files that have been infected by Ramnit, it will display a new file by adding a string MGR after the file name (see Picture 6).
Picture 6. Examples of files that have been infected with
viruses and virus duplicate files
Uniting We Stand, Divorced Friends reconcile
Like the saying goes cigarette advertising, United We Stand Divorced Friends reconcile. By the time the computer is infected Ramnit, he would invite his friends like Virut or Sality who have the ability to infect application files (EXE), so that in a single application file (EXE) often found infected with more than one virus other than Ramnit (example: Sality or Ramnit), if this happens then you will be reminded of another adage. Have fallen, crushed and torn pants stairs again.
PREVENTION STEPS
How to make your PC immune to attack Ramnit?
From the results of lab analysis Vaksincom, current virus Ramnit "always" using the master file with the same name ie "WaterMark.exe" although its storage location varies depending on the variant that infects the computer and create files "Explorermgr.exe" in directory [C: \ Windows], the file "Explorermgr.exe" is created if Ramnit managed to infect a file "Explorer.exe".
So that your computer does not become victims of malignancy Ramnit, here are some tips and tricks for your computer to be immune from attack Ramnit.
1.Buat dummy folder (empty folder) with the name "WaterMark.exe" and "svchost.exe" in the usual location in the drill by a virus, then change the file attributes to Hidden, System and Read Only. This step is done so that Ramnit can not make the main virus file in the same location.
2.Buat file "Recycler" on each drive, then change the attributes to Hidden, System and Read Only. This step is done so that Ramnit can not create a master file (in the form of an EXE extension and CPL) to a RECYCLER file. RECYCLER because this form of file (not a FOLDER) then Ramnit will not be able to make virus file in that location.
3.Buat 2 (two) the registry key in the following locations:
HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows NT \ CurrentVersion \ Image File Execution Options (see figure 7)
Key: Explorermgr.exe and WaterMark.exe
String value: Debugger
Type: REG_SZ
Data value: ntsd-d
Picture 7. String registry to block Ramnit not to be active in the computer
This step is done, so that the script / code of existing viruses on Ramnit virus file can not be executed, so Ramnit not be active in memory.
Kanuragan for USB Flash
As noted previously, Ramnit will also spread itself by making use of USB Flash media to make some virus files, the following tips and tricks to Ramnit can not create a master file into a USB Flash Media
1. Khusus for files with extensions EXE / DLL / HTM / HTML should be in a compress using the program WinZip / WinRAR so that the virus does not infect the file, if necessary use a password.
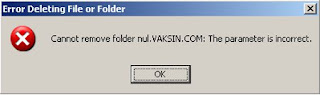
2. Buat empty folder with the name [autorun.inf]. In order for the [autorun.inf] is not deleted by a virus create an empty folder in the folder [autorun.inf] with characters that are not recognized by Windows as CON and NUL. If the folder [autorun.inf] is in the clear will of failure to display an error message. We recommend that you change the attributes to Hidden, System and Read Only (see Picture 8 and 9)
Picture 8. Make the autorun.inf file
Picture 9. Error message when deleting the autorun.inf file
3. Buat empty folder with the name "Copy of Shortcut to (1). Lnk", "Copy of Shortcut to (2). Lnk", "Copy of Shortcut to (3). Lnk" and "Copy of Shortcut to (4 ). lnk ", then change the attributes to Hidden, System and Read Only.
4. Buat file "Recycler", then change the attributes to Hidden, System and Read Only.
5. Buat MSO.SYS empty folder with the name, then change the attributes to Hidden, System and Read Only.








0 comments:
Speak up your mind
Tell us what you're thinking... !